Log_year If set, the four-digit 12 months will be logged in the (non-syslog) sudolog file. Long_otp_prompt When validating with a One Time Password scheme corresponding to S/Keyor OPIE, a two-line immediate is used to make it easier to chop and paste the problem to an area window. It's not as pretty because the default but some individuals find it more convenient. Mail_all_cmnds Send mail to the mailto user every time a user attempts to run a command via sudo . No mail will be despatched if the user runs sudo with the -l or -v possibility until there is an authentication error and the mail_badpass flag can also be set. Mail_always Send mail to the mailto user every time a user runs sudo. Mail_badpass Send mail to the mailto user if the user running sudo doesn't enter the correct password. Mail_no_host If set, mail will be sent to the mailto user if the invoking user exists in the sudoers file, however is not allowed to run instructions on the current host. Mail_no_user If set, mail will be sent to the mailto user if the invoking user is not in the sudoers file. Match_group_by_gid By default, sudoers will lookup every group the user is a member of by group-ID to find out the group name . The resulting record of the user's group names is used when matching teams listed in the sudoers file. This works nicely on methods where the variety of teams listed in the sudoers file is bigger than the number of groups a typical user belongs to. On such systems it may be sooner to use the match_group_by_gid flag to keep away from resolving the user's group-IDs to group names. Note that if match_group_by_gid is enabled, group database lookups carried out by sudoers will be keyed by group name as opposed to group-ID. Here we override some of the compiled in default values. We need sudo to log via syslog using the auth facility in all instances and for instructions to be run with the goal user's home listing as the working listing. We don't need to subject the complete time employees to the sudo lecture and we want to allow them to run instructions in a chroot "sandbox" via the -R choice. User millert need not provide a password and we do not want to reset the LOGNAME or USER surroundings variables when running instructions as root. Lastly, we disable shell escapes for the instructions in the PAGERS Cmnd_Alias (/usr/bin/more, /usr/bin/pg and /usr/bin/less) .
Note that this will not successfully constrain users with sudo ALL privileges. Log_host If set, the host name will be included in log entries written to the file configured by the logfile setting. Log_input If set, sudo will run the command in a pseudo-terminal and log all user enter. Anything despatched to the standard enter will be consumed, regardless of whether or not or not the command run through sudo is definitely reading the standard enter. This might have unexpected outcomes when utilizing sudo in a shell script that expects to process the usual enter. For extra details about I/O logging, see the I/O LOG FILES section. Log_output If set, sudo will run the command in a pseudo-terminal and log all output that is despatched to the screen, just like the script command. Log_server_keepalive If set, sudo will allow the TCP keepalive socket option on the connection to the log server. This permits the periodic transmission of keepalive messages to the server. This setting is just supported by version 1.9.0 or higher. Umask_override If set, sudo will set the umask as laid out in the sudoersfile without modification. This makes it attainable to specify a umask in the sudoers file that's more permissive than the user's own umask and matches historical habits. If umask_override is not set, sudo will set the umask to be the union of the user's umask and what is specified in sudoers.
Use_netgroups If set, netgroups (prefixed with '+'), may be used instead of a user or host. For LDAP-based sudoers, netgroup assist requires an costly sub-string match on the server unless the NETGROUP_BASEdirective is present in the /etc/ldap.conf file. If netgroups usually are not wanted, this option may be disabled to reduce the load on the LDAP server. Use_pty If set, and sudo is running in a terminal, the command will be run in a pseudo-terminal (even if no I/O logging is being done). If the sudo process is not hooked up to a terminal, use_pty has no impact. By running the command in a separate pseudo-terminal, this assault is no longer attainable. Pam_session On methods that use PAM for authentication, sudo will create a model new PAM session for the command to be run in. Unless sudo is given the -i or -s choices, PAM session modules are run with the "silent" flag enabled. This prevents last login information from being displayed for each command on some systems. Disabling pam_session could also be wanted on older PAM implementations or on working techniques the place opening a PAM session changes the utmp or wtmp files. If PAM session support is disabled, resource limits is in all probability not up to date for the command being run. This setting is simply supported by version 1.8.7 or higher. Targetpw If set, sudo will prompt for the password of the user specified by the -u option instead of the password of the invoking user when running a command or modifying a file.
Note that this flag precludes the use of a user-ID not listed in the passwd database as an argument to the -u choice. Tty_tickets If set, customers must authenticate on a per-tty basis. With this flag enabled, sudo will use a separate record in the time stamp file for each terminal. If disabled, a single document is used for all login periods. This option has been outmoded by the timestamp_typeoption. Number of minutes that can elapse earlier than sudo will ask for a passwd once more. The timeout may embrace a fractional element if minute granularity is inadequate, for instance 2.5. Set this to 0 to all the time prompt for a password. If set to a price less than zero the user's time stamp won't expire until the system is rebooted. This can be used to allow customers to create or delete their own time stamps via "sudo -v" and "sudo -k" respectively. Umask File mode creation mask to use when operating the command. Negate this feature or set it to 0777 to stop sudoers from altering the umask. Unless the umask_override flag is set, the actual umask would be the union of the user's umask and the worth of the umasksetting, which defaults to 0022. This ensures that sudo by no means lowers the umask when operating a command.
If umask is explicitly set in sudoers, it'll override any umask setting in PAM or login.conf. If umask is not set in sudoers, the umask specified by PAM or login.conf will take priority. The umask setting in PAM is not used for sudoedit, which doesn't create a new PAM session. Prior to version 1.8.21, surroundings variables with a worth starting with () have been at all times removed. Beginning with version 1.eight.21, a sample in env_delete is used to match bash shell features instead. Since it isn't attainable to dam all probably dangerous surroundings variables, use of the default env_reset behavior is encouraged. The sudoers plugin contains sudoedit assist which allows customers to securely edit files with the editor of their alternative. As sudoedit is a built-in command, it should be specified in the sudoers file and not using a leading path. However, it might take command line arguments just as a normal command does. Wildcards utilized in sudoedit command line arguments are expected to be path names, so a ahead slash ('/') won't be matched by a wildcard.
One instance of a credential is a Kerberos ticket. This setting is just supported by version 1.8.eight or greater. Since time stamp information live in the file system, they will outlive a user's login session. When the tty_tickets choice is enabled, the time stamp report includes the gadget variety of the terminal the user authenticated with. This supplies per-tty granularity but time stamp data nonetheless might outlive the user's session. The time stamp record also includes the session ID of the method that last authenticated. This prevents processes in several terminal sessions from using the identical time stamp record. It also helps cut back the possibility that a user will be able to run sudo without getting into a password when logging out and again in once more on the identical terminal. If, nonetheless, the env_reset possibility is disabled, any variables not explicitly denied by the env_check and env_delete options are inherited from the invoking process. In this case, env_check and env_delete behave like a blacklist. Environment variables with a worth starting with () are all the time eliminated, even if they don't match one of the blacklists. Since it's not potential to blacklist all potentially dangerous setting variables, use of the default env_reset habits is inspired. Lecture_status_dir The directory in which sudo shops per-user lecture status files. Once a user has received the lecture, a zero-length file is created in this listing so that sudo will not lecture the user once more.
This listing shouldn't be cleared when the system reboots. The default is to use the system's default certificate authority database. This setting has no impact unless log_servers is set and the distant log server is secured with TLS. SETENV and NOSETENV These tags override the value of the setenv flag on a per-command basis. Note that if SETENV has been set for a command, the user may disable the env_reset flag from the command line via the -E possibility. Additionally, setting variables set on the command line usually are not topic to the restrictions imposed by env_check, env_delete, or env_keep. As such, only trusted customers should be allowed to set variables in this manner. If the command matched is ALL, the SETENV tag is implied for that command; this default could additionally be overridden by use of the NOSETENV tag. If sudo is run by root and the SUDO_USER environment variable is ready, the sudoers policy will use this worth to find out who the precise user is. This can be used by a user to log instructions through sudo even when a root shell has been invoked. It also allows the -eoption to stay helpful even when invoked by way of a sudo-run script or program.
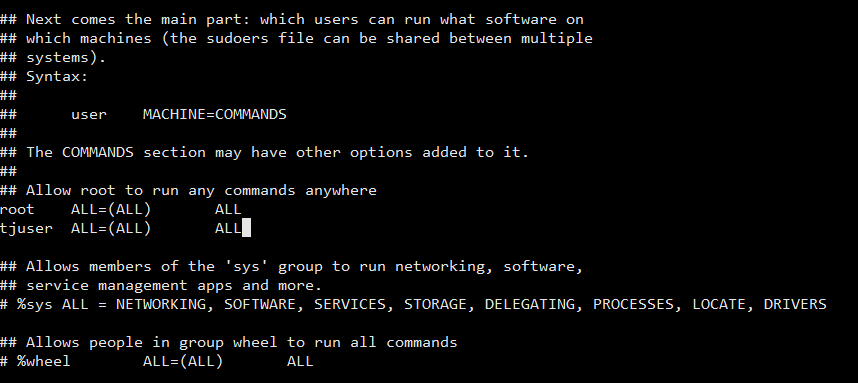
Note, however, that the sudoers file lookup is still accomplished for root, not the user specified by SUDO_USER. As sudoeditis a built-in command, it have to be laid out in the sudoersfile without a leading path. Wildcards used in sudoeditcommand line arguments are anticipated to be path names, so a ahead slash ('/') is not going to be matched by a wildcard. If pam_session, pam_setcred, and use_pty are disabled and I/O logging has not been configured, sudo will execute the command directly as a substitute of running it as a baby process. It additionally permits the -e choice to stay helpful even when invoked via a sudo-run script or program. Now you'll find a way to login the WSL2 as a root . The issue was happened, since I modified /etc/sudoers file with visudo command. The drawback is, by default, visudo command begin nano editor that I'm not conversant in. It has two option for save DOS and MAC . I'm using Linux How can I choose the one. Mac is closer to Linux, so I select it. These process provides particular character on that file. Even if I accurately configured it, it nonetheless emit error for each line apart from remark traces. Unless the timestamp_type possibility is set to "global", the time stamp document additionally contains the session ID of the process that final authenticated. On methods where a course of's start time could be queried, the beginning time of the session leader is recorded in the time stamp document. If no terminal is present or the timestamp_type possibility is ready to "ppid", the start time of the parent process is used instead. In most circumstances this can forestall a time stamp record from being re-used with out the user coming into a password when logging out and back in once more. When log_servers is ready, occasion log data will be logged both domestically as nicely as remotely, but I/O log data will solely be logged remotely.
If multiple hosts are specified, they will be tried in reverse order. Please note that the record of environment variables to remove varies based on the working system sudo is operating on. Sudoers uses per-user time stamp recordsdata for credential caching. The user could then use sudowithout a password for a short time frame . By default, sudoers uses a separate report for each terminal, which implies that a user's login periods are authenticated individually. The timestamp_type possibility can be utilized to choose out the type of time stamp record sudoers will use. NOSETENV These tags override the value of the setenvoption on a per-command foundation. Note that if SETENV has been set for a command, the user might disable the env_reset possibility from the command line via the -E option. On methods that help PAM where the pam_env module is enabled for sudo, variables in the PAM setting may be merged in to the environment. If a variable in the PAM environment is already present in the user's setting, the worth will solely be overridden if the variable was not preserved by sudoers. When env_reset is enabled, variables preserved from the invoking user's surroundings by the env_keep record take priority over these in the PAM surroundings. When env_reset is disabled, variables current the invoking user's setting take priority over those in the PAM environment except they match a pattern in the env_delete record. Pam_ruser On techniques that use PAM for authentication, sudo will set the PAM distant user value to the name of the user that invoked sudo when the pam_ruser flag is enabled. As a special case, if the -i possibility is specified, sudoers will initialize the environment regardless of the value of env_reset.
The DISPLAY, PATH and TERM variables stay unchanged; HOME, MAIL, SHELL, USER, and LOGNAME are set based on the goal user. On AIX , the contents of /etc/environment are also included. All other setting variables are removed except permitted by env_keep or env_check, described above. In this tutorial I gave you an entire overview on finest practices to make use of and modify sudoers file. The steps to add user to sudoers with proper syntax and completely different sensible examples, about different alias, and executing sudo instructions without password prompt. In manufacturing environment, sudoers file are dealt with very cautiously. The default sudoers file include plenty of default entries and it may break if you do not modify the this file correctly. What you'll have to do is login as "root" through the use of the command "su -l". The "-l" means it ought to login usually. The default user for the su command is root. Then you will enter the password for the basis account, giving you a shell immediate where you presumably can run any command as root. Once you may be logged in as root, the system is open to vulnerabilities. It is best to supply rights to the non-root user for the only function to run a desired command/program. However, your username should be in the sudoers file. The sudoers file is a file Linux and Unix directors use to allocate system rights to system users. This permits the administrator to control who does what. Remember, Linux is constructed with safety in thoughts. When you want to run a command that requires root rights, Linux checks your username against the sudoers file. This occurs when you type the command "sudo".